simple, effective Authentication Technology
Next generation authentication for your websites, VPNs and apps
The world’s first patented omni-factor authentication™. Protect your websites, VPNs and apps with an industry leading multi-factor authentication solution all verified by the user sending a simple text message.
Get A multi-factor authentication solution that offers protection, ease of implementation and no learning curve
TextKey® is an award winning, patented next-generation multi-factor authentication™ system that is highly secure, simple to install and easy to use. It can be used to protect web sites, mobile devices, Virtual Private Networks (VPNs) or any other data that requires privacy, confidentiality or restricted access.
The first generation of two-factor authentication was the "token" or "key fob" that required a user to carry an extra device with them to verify their identity. Users disliked carrying extra devices and it was proven to be easily hackable.The second generation of two-factor authentication is the "soft token" that uses a cell phone or other device as the authentication mechanism. These are an improvement, but are complex to install & maintain and expensive. Plus, they are less secure because they can be "spoofed" and leave an opening on the web site login that can be hacked because of the immense power of hacking programs on a standard desktop PC. Now, TextPower introduces the next generation of authentication - the patented technology of TextKey®.
TextKey® is the only multi-factor authentication service that works by sending a message FROM your cell phone for verification. It uses patented technology that can defend your websites, VPNs and Apps from attack by having someone verify their identity simply by sending a text message FROM their cell phone.
WHAT MAKES TEXTKEY® DIFFERENT
Ironclad protection.
David Strom
Network World Magazine
"Hack-Proof" TextKey Turns SMS Authentication on Its Head
Neil J. Rubenking
PC Magazine
METHODOLOGY
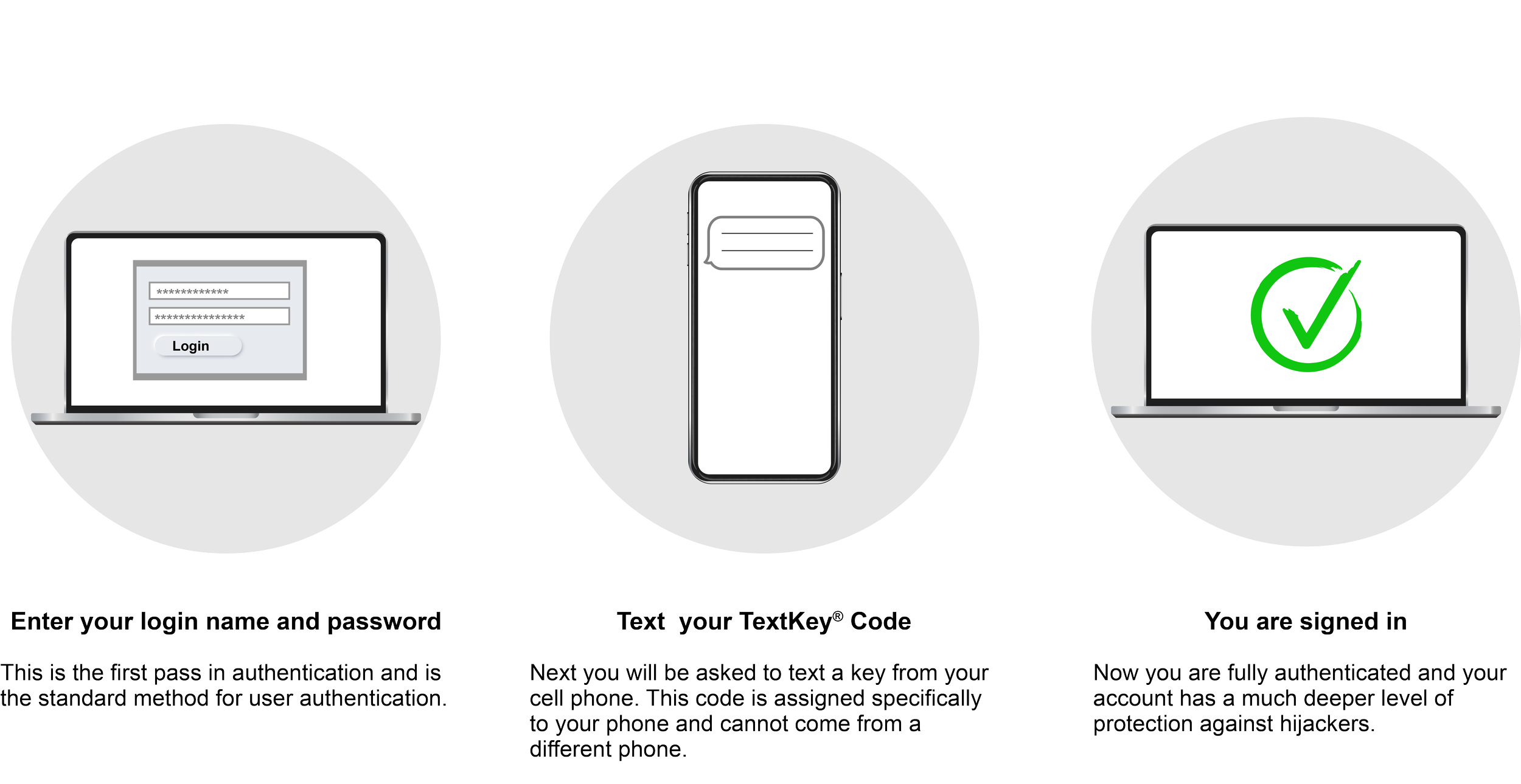
Unlike traditional 2 Factor Authentication systems, with TextKey® users send a simple text message (SMS) FROM their cell phone to authenticate their identity making authentication more secure.
7 FACTORS OF AUTHENTICATION
TextKey® provides up to 7 distinct factors of authentication, including the phone’s fingerprint (its unique device identifier), mobile number, PIN and a one-time unique key making the online property virtually unhackable.
7-Factors
EASY TO INSTALL
TextKey® replaces complex, costly and high-maintenance systems with a simple approach that leverages the power of sophisticated engineering and a cell phone’s fingerprint.
AFFORDABLE
TextKey® eliminates significant up-front expense of other two-factor authentication systems by offering a way for companies of any size to implement authentication quickly and inexpensively.
Don’t compromise on security. Get never before seen unprecedented 7 factors of multi-factor authentication for your online properties. Request a TextKey® product demonstration today.
Who needs TextKey®?
Small and medium-sized businesses (SMBs), enterprises, financial institutions, medical facilities or others that want to protect intellectual property, sensitive records, transactions or other important information from theft or illegal access.
Don’t companies already protect their websites?
Most websites are only protected by the standard user ID and password process simply because more effective protection has been too difficult, cumbersome or expensive for the average business to implement. The established and industry-accepted best practice for protecting a website from intruders that goes beyond ID/password protection is a “two-factor authentication” system.
What is Two-Factor Authentication system?
Two-factor authentication is a security process in which the user provides two means of identification. The first factor usually consists of a login name and password and the second consists of something the user has like a phone. In the case of TextKey®, our multi-factor authentication enhances the security of the user's online accounts by using their phone and only their phone to verify their identity. This prevents anyone but the user from accessing their accounts, even if they know the user's login name and password.
If it’s better why don’t all web sites use Two-Factor Authentication?
Two-factor authentication systems can be complex, difficult to install, constant work to maintain and are typically very costly. Only companies with significant information technology resources have been able to implement these systems in the past.
What makes TextKey® multi-factor authentication different?
TextKey® is a next-generation authentication system. It replaces complex, costly and high-maintenance systems with a simple approach that leverages the power of advanced messaging technologies and a cellular phone’s “fingerprint”. Many companies that have a need for security haven’t taken the appropriate steps to secure their environments because of the complications and expense. TextKey® offers a way for companies of any size to implement multi-factor authentication quickly and inexpensively.
Why is TextKey® more secure than other authentication systems?
Every cellular phone ever manufactured contains a unique device identifier (a “UDID”) that serves as the “fingerprint” of that device. While hacking or spoofing may work on common two-factor authentication systems because they receive, not send, text messages, the TextKey® system eliminates this hacking by using the fingerprint of the phone to verify that the message is being sent by a legitimately authorized phone and not a "spoofed" number. A text message cannot be sent into the TextKey® system without the cell phone carrying the correct UDID.Furthermore, two-factor authentication systems rely on information being input into a browser by a user. Typically someone using a cell phone receives a text message containing an authorization code and then must enter the code that appears on the token or cell phone’s screen into a field on the web page. By definition this opens the process to “man-in-the-middle” (MITM) or “man-in-the-browser” (MITB) hacks that compromise the security of the entire process. TextKey® uses a patented process that completely eliminates any information being entered into, or shared through, the browser. All communication occurs on a secure server-to-server connection outside of the browser environment and thus excludes, by definition, any possibility of MITM or MITB attacks.
Is TextKey® difficult to set up on my website?
If your web site already uses a simple user ID and password system, more than 90% of the work is done.
How long does it take to implement it?
Compared to other 2FA systems that takes days or weeks to implement, TextKey® can be installed on a typical website in a few hours. TextKey® is designed so that our infrastructure does the heavy lifting; the majority of the code and processing occur on our system, not yours. TextKey® doesn’t require any hardware or software that might interfere with your regular operations. Implementations may vary based on the complexity of your application, desired features, etc., but the only thing that is required for TextKey® to work is to have a cellular phone number associated with each user ID and to have that information registered on our system.
DEVELOPER RESOURCES: HERE ARE SOME RESOURCES TO GET YOU STARTED ON PROTECTING YOUR LOGINS AND UNDERSTANDING THE CAPABILITIES OF TEXTKEY®
TEXTKEY® CAN’T BE “SPOOFED”
BY OTHER CELL PHONES!
THE TEXTKEY® DIFFERENCE IS THAT THE CODE IS DISPLAYED ON THE LOGIN PAGE – IT MUST BE SENT VIA TEXT FROM THE CELL PHONE ASSOCIATED WITH THE LOGIN CREDENTIALS!
More secure than a token
Simple to implement
A fraction of the cost of token systems
Captures the cell phone number of attempted break-ins
WHAT IS SPOOFING?
Spoofing, in this scenario, means using technical trickery to fool a system into believing that a phone call or text message (SMS) was sent to, or received by, a person or device that it actually was not. Spoofing does work when SIMs (subscriber identification modules) that provide the identity to phones are cloned. Spoofing does not work in the other direction, however, because the phone’s unique identification, which is burned into the chip that powers the phone, carries a “fingerprint” that cannot be spoofed. It is this “fingerprint” that identifies the phone to the carrier network, not the phone number.
SPOOFING MAY WORK TO CIRCUMVENT OTHER SERVICES BUT TEXTKEY™ ISN’T SUBJECT TO IT FOR SOME VERY FUNDAMENTAL REASONS.
First of all, it’s important to understand that when people are spoofing they are doing so by trying to modify the “SenderID” field on an SMS. It’s not that hard to do – in fact the GSM standard actually allows that field to be set manually. Hackers might even try sending the message out to a foreign carrier and looping it back into a US carrier with the Sender ID modified but that won’t work either; TextPower’s (and other US aggregators) short codes aren’t accessible through foreign carriers.
Even with all that, however, changing the SenderID field won’t allow the system to be hacked. Here’s why:
Carriers don’t identify mobile devices by phone numbers – they see them as unique device IDs (a “UDID”). When a message is sent from a mobile device through TextPower’s system the message goes directly from the user’s phone through the carrier to TextPower. The originating phone number supplied to TextPower by the carrier comes directly from the carriers’ database, which associates the phone number with the device ID. Anyone trying to spoof the phone number will be sending it from a different device ID and thus won’t match in the database, causing it to be rejected (and, in all likelihood, put on a fraud list) by the carrier. Sending a text from a spoofing web site, or from a phone that’s been modified, will still come from a different device ID.
Next, while text messages are sent unencrypted from the phone to the cell site, once it hits the carrier’s network all communications are in a fully secured mode and can’t be intercepted. So the spoof would have to be from the phone to the cell site, which, as noted above, can’t happen with a short code and different phone.
SO, COULD CLONING/SPOOFING OF A UDID OCCUR?
So the question arises, could you clone the guts of a phone so that it would have the same UID as someone else’s phone? Yes, you could, but that would be very expensive and extremely difficult to do (cloning a SIM is easy, cloning a device ID is not – be careful not to confuse the two). Moreover, if someone did clone a device as soon as it was on the carrier’s network at the same time as the original device they would both be blocked and probably put on a fraud list immediately.
WILL TEXTKEY® STILL WORK IF THE UDID WAS CLONED/SPOOFED?
Finally, even if you were to undergo the extreme difficulty of cloning the guts of a phone to get the identical UID, and then somehow figured out how to avoid getting the device blocked when the original one is on the network, too, you’d then still have to have the ID and PW for that user, know what the code is that’s displayed on the web page at that moment and then know what to do with the code – for example, they would have to know which of many short codes we offer it would have to get sent to.
SO IS TEXTKEY® COMPLETELY UNHACKABLE?
No, but it’s vastly more secure than many other methods and is not subject to spoofing. We believe that this is a rock-solid solution that is secure, easy to implement and an order of magnitude less expensive than other solutions.
Protect your websites, VPNs and apps. TextKey® is easy to install and affordable. Contact us today for more information.